USB ドライブ、外付けハードドライブ、その他のポータブルデバイスなどのリムーバブルメディアは、OT(Operational Technology:運用技術)環境にとって重要かつ見過ごされがちな脅威です。DarkReadingのレポートでは、国家がUSBに回帰し、BYODサイバー攻撃でUSBを使用して、高度に保護された政府組織を侵害しつつあることを明らかにし、これを「サイバーセキュリティにおける最も奇妙な傾向」と呼んでいます。
リムーバブル・メディアは従来のネットワーク・ベースの防御をバイパスするため、マルウェアをエアギャップやセグメント化されたシステムに直接送り込み、OTや重要インフラ環境が依存するセキュリティ・モデルを悪用します。SANS 2025 ICS/OT Cybersecurity BudgetReportによると、2024年には、ICS(産業用制御システム)を標的としたサイバー攻撃における初期ベクターの20.3%をリムーバブルメディアが占め、全OT侵害の15.2%はリムーバブルメディアから発生しています。
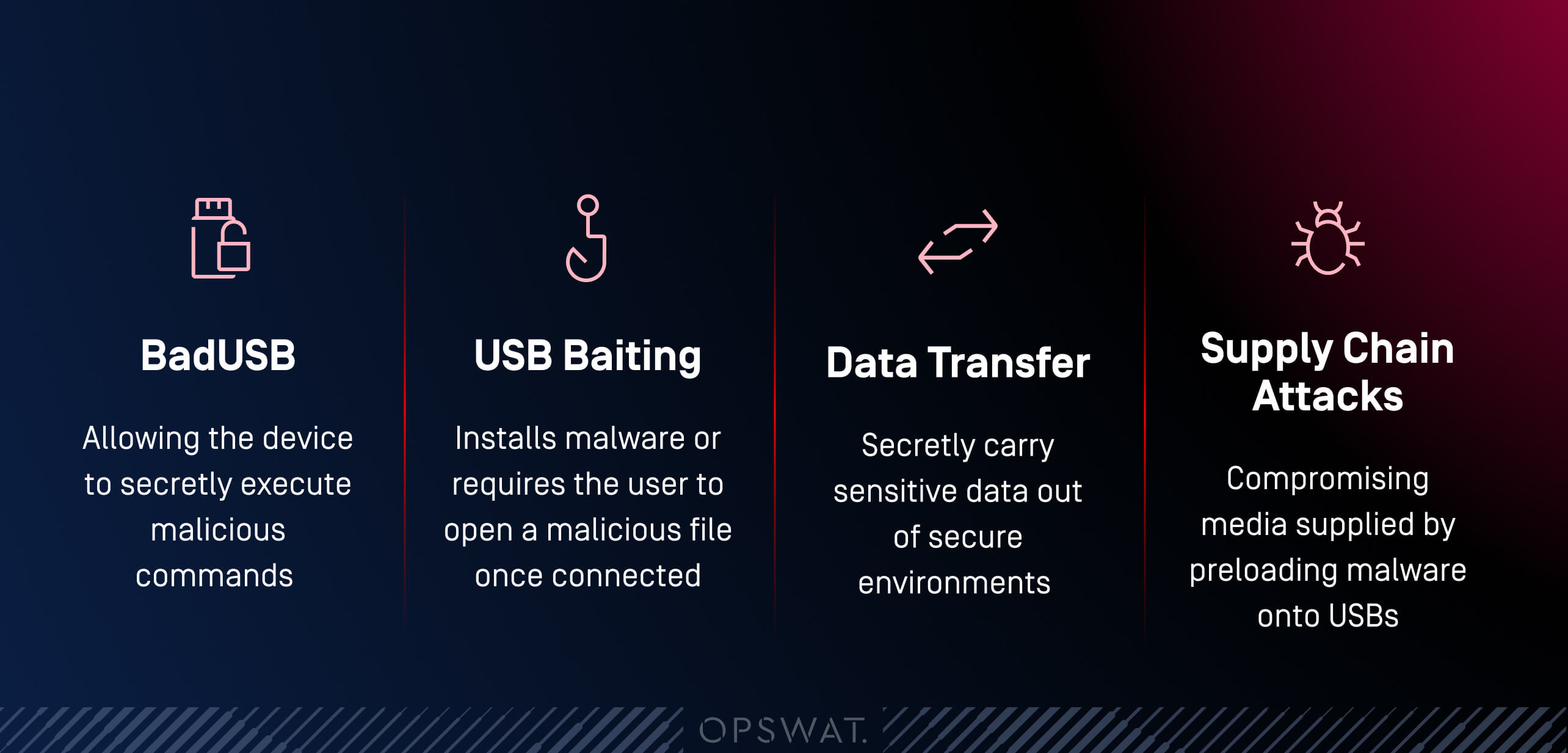
Media悪用する脅威の手口
リムーバブルメディアを使って従来のセキュリティ管理を迂回し、検知を回避します:
- BadUSB: USB デバイスのファームウェアを、キーボードやネットワークカードなどの正規のデバイスを模倣するようにプログラムし直し、デバイスが密かに悪意のあるコマンドを実行できるようにします。
- USB おとり:マルウェアをインストールしたり、接続後に悪意のあるファイルを開かせたりします。
- データ転送:マルウェアの転送に使用されるのと同じメディアをエアギャップ・システムに使用し、機密データをセキュアな環境から密かに持ち出します。
- Supply Chain 攻撃:製造時や配布時にマルウェアをUSBにプリロードすることで、ベンダーや請負業者から提供されたメディアを侵害します。
クリティカル・システムがかつてないほど脆弱になった理由
従来のアンチウイルスはもはや有効ではありません。
単一のウイルス対策エンジンでは、平均45.4%の検出率しか達成できない。単一のアンチウイルスソリューションは、シグネチャベースの検出アプローチと既知のマルウェアの限られたデータベースに依存しているため、現代の回避的でAI主導のマルウェアに対しては不十分です。
ゼロデイ・エクスプロイトのリスク
パッチやシグネチャがなく、攻撃を検知するための情報が不足しているため、ゼロデイ攻撃は被害が発生してから初めて検知されることが多いです。予防ではなく、検知だけに頼っていると、重要なインフラは非常に脆弱なままになってしまいます。
疑わしい出所のファイル
リムーバブル・メディアに保存された不審な外国製のファイルは、国家的な敵対勢力によるマルウェア以上のリスクをもたらす可能性があります。一見、安全に見えるが、特定の場所から発信されたファイルを処理したり、ソフトウェアを使用したりすることは、組織が規制コンプライアンスを満たせず、多額の罰金を科される危険性があります。
回避的でAI主導のマルウェア
攻撃者は、マクロやメモリ駆除などの一般的な回避手法から、挙動を変化させるAIベースのマルウェアまで、最新のテクノロジーを駆使して検知困難なマルウェアを開発し続けています。このような洗練されたレイヤーには、検知よりも防御を優先する多層的なソリューションが必要です。
ヒューマンエラーとデータ漏洩
リムーバブル・メディアは、パスワード、重要なビジネス・データ、極秘コンテンツなどの機密データを持ち運び、有害なデータ漏洩につながる可能性があります。このような行為は、データ漏洩やコンプライアンス違反の大きな原因となっています。
マルウェアの侵入を食い止める
MetaDefender Kiosk™は、過酷な環境下でも様々な運用環境の要件を満たす5つのフォームファクタを備え、特に重要なエアギャップ環境において、使用前にすべてのリムーバブルメディアがスキャンされ、検証されることを保証する物理的なゲートキーパーとして機能します。20以上のメディアタイプをサポートするMetaDefender キオスクは、USB ドライブ、メモリカード、ハードドライブ、CD、DVDを含む幅広いリムーバブルメディアをスキャンします。
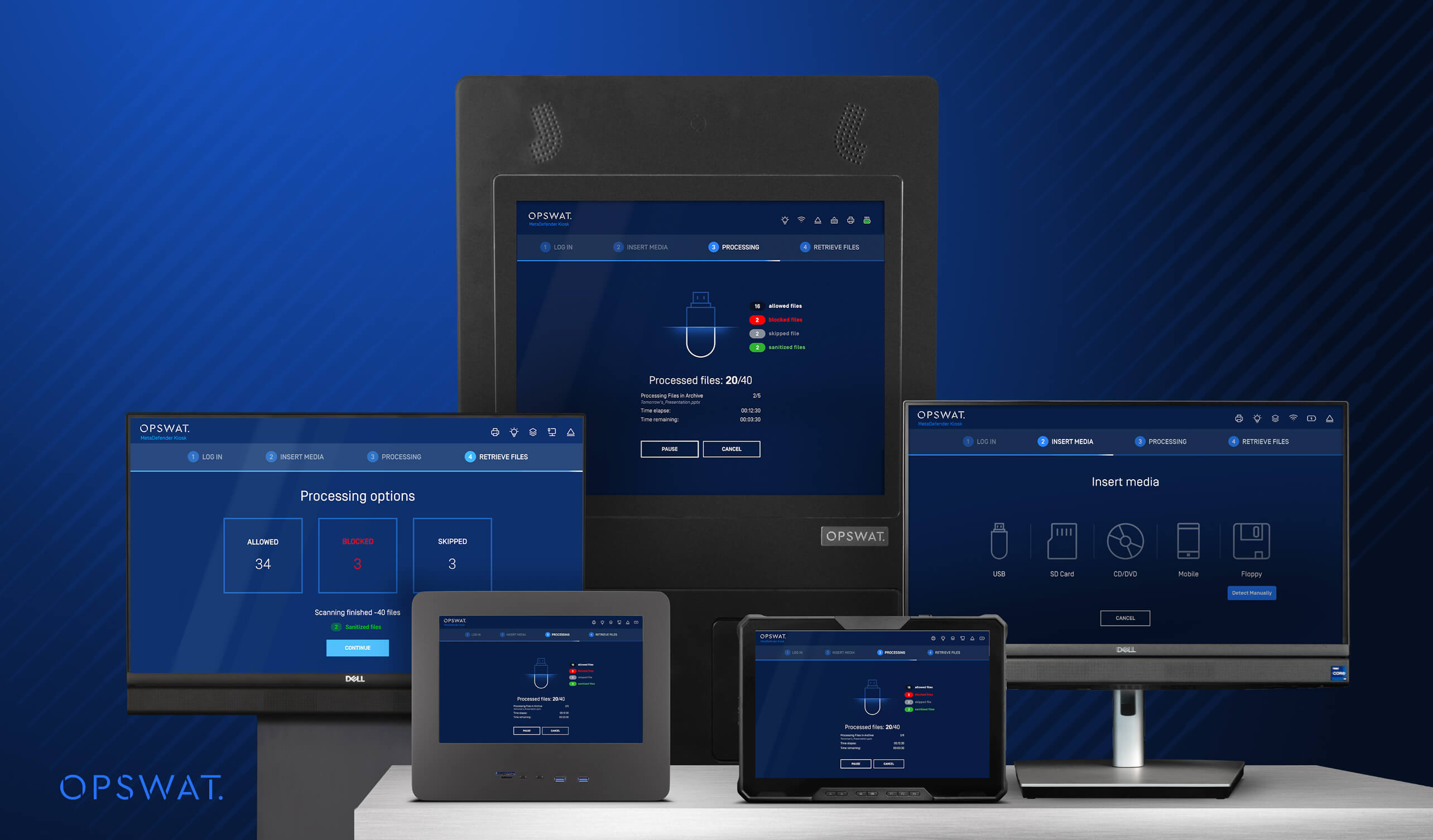
最も巧妙なリムーバブルメディアの脅威からOT資産を守るための保護を提供する、実績のある世界的に信頼されている技術を備えています。
複数のエンジンによるAdvanced Threat Detection
30種類以上のマルウェアエンジンで最大99.2%に達する検出率を誇るMetascan™Multiscanning 、さまざまなサイバー脅威からの保護を強化し、発生までの時間を短縮し、誤検出の可能性を低減します。
未知の脅威から身を守る予防技術
従来のスキャンソリューションが未知の脅威を検出できないのに対し、Deep CDR™は機能を維持したままファイルをサニタイズおよび再生成することで、これらの脅威を防御する技術です。200以上のファイルタイプをサポートし、ゼロデイ・エクスプロイトや回避型マルウェアなど、検出されない脅威の防止を支援します。
コンプライアンス違反を回避するためのファイル起源の検出
Country-of-Origin テクノロジーは、メタデータとフィンガープリントを分析することにより、ファイルの地理的な出所を検出します。ファイルの地理的な出所を確認することで、企業はコンプライアンス違反を回避することができます。
機密データ漏洩の防止
機密データを保護するため、Proactive DLP™は、重要なエアギャップ・ネットワークとの間で転送される前にファイルをチェックし、カスタム正規表現を使用して機密データや秘密データをブロックします。
既知のファイル脆弱性の検出
MetaDefender Kiosk 、アクティブなデバイスから収集した3,000,000以上のデータポイントと、30,000以上の関連するCVE(重大度情報)により、ファイルやソフトウェアをエアギャップを通過させる前に、一般的な脆弱性をチェックします。
統合された周辺機器とMedia 保護とその先
MetaDefender Kiosk 、MetaDefender ソリューションとKiosk 、リムーバブルメディアおよび周辺機器向けの多層セキュリティを実現します。MetaDefender Managed File Transfer MFT)™とシームレスに統合され、安全に処理されたファイルのセキュアな転送を提供します。
My OPSWAT™Central Management 、アプライアンスの設定、スキャンポリシーの設定と実施、複数のキオスク上での詳細な監査ログの生成を、すべて1枚のガラスから行うことができます。MetaDefender Kiosk 、その高度なスキャン機能に加えて、一元化された監査可能なログと一貫したポリシーの実施により、NIST、IEC 62443、ISO 27001、NERC CIPを含む厳格なOT特有の規制基準へのコンプライアンスを支援します。MetaDefender Netwall 、リアルタイムのOTデータへのアクセスを提供し、OT環境への安全なデータ転送を可能にすると同時に、ネットワークを介した脅威からOT環境を守ります。
MetaDefender Media Firewall™は、挿入されたポータブルメディアのブートセクタとファイルコンテンツが、使用前にMetaDefender KioskTMによって検査、監査、サニタイズされ、承認されることを保証します。MetaDefender Endpoint Validation™またはMedia Validationは、リムーバブルメディアが強制されたポリシーの下でスキャンされたことも確認できます。
エンド・ツー・エンドのMedia 保護
OPSWAT 、1,900を超える重要なインフラ組織との実績により、進化するリムーバブルメディアの脅威に対する戦略的優位性を提供し続けています。MetaDefender Kiosk 、USB ドライブやその他のメディアデバイス上のデータのチェックポイントとして機能し、安全なネットワークに出入りする前にデジタルデータを分析、制御、サニタイズします。
MetaDefender Kiosk どのように現代のサイバー脅威からOT環境を守ることができるのか、詳細を知り、ライブデモを見るには、今すぐ当社のエキスパートにデモを予約してください。

