MeitY(電子情報技術省)傘下のCERT-In(インド・コンピュータ緊急対応チーム)は、2008年の情報技術改正法に基づいて指定されて以来、サイバーセキュリティの国家機関としての役割を着実に拡大してきた。
2024年、CERT-InはSBOMSoftware 部品表)に関する初の専用ガイドラインを発行し、最小限の要素、形式、および実装要件を定義した。
それからわずか1年後の2025年7月、バージョン2.0では対象範囲が大幅に拡大され、SBOM、QBOM、CBOM、AIBOM、HBOMに適用範囲が拡大され、安全なソフトウェア・サプライチェーンが国家のレジリエンス戦略の中核としてさらに確立された。
CIOとCISOにとって、これらのガイドラインは、運用、財務、および規制上の結果をもたらす。組織は、監査に対応できる SBOM の実践を実証し、ベンダーとパートナーをコンプライアンス要件に適合させ、SBOM を大規模に管理するための自動化を導入する準備を整えなければならない。
この記事では、CERT-In SBOMガイドライン準拠を達成するためのステップ・バイ・ステップのロードマップを提供し、インド企業やインドで事業を展開するグローバル組織のスコープ、技術基準、ベンダー選定、ベストプラクティスを網羅する。
- CERT-In SBOM ガイドライン:適用範囲、適用可能性、主要要件
- OPSWAT SBOMがCERTイン要件にどのように役立つか
- Software コンポーネントの CERT-In SBOM コンプライアンスへの適合
- CERT-Inの下で受け入れられたSBOMフォーマットと技術標準
- SBOMコンプライアンス・ベンダーの評価と選び方
- シームレスなSBOM実装のベストプラクティス
- 自動化、遵守、保護:SBOM管理へのOPSWAT アプローチ
- MetaDefender Software
- よくある質問
- セクター別の考察:金融機関、Supply Chain、重要インフラストラクチャー
- 次なる課題は?サートインSBOMガイドラインへの備えが不可欠
CERT-In SBOM ガイドライン:適用範囲、適用可能性、主要要件
CERT-Inとは何か、なぜSBOMガイドラインを発行したのか?
CERT-Inはインドの国家サイバーセキュリティ機関である。そのSBOMガイドラインは、サプライチェーンのセキュリティを強化し、ソフトウェアコンポーネントの可視性を向上させ、脆弱性への迅速かつ標準的な対応を保証することを目的としている。
CERT-Inとは何か、なぜSBOMガイドラインを発行したのか?
コンプライアンスは、政府、公共部門、基幹業務、ソフトウェア輸出業者、ソフトウェア・ライフサイクル全般にわたる開発者、インテグレーター、再販業者に適用されます。
CERT-InガイドラインによるSBOMのCore 要素
ガイドラインによると、SBOMは以下のようなデータを含まなければならない:
- コンポーネント名、バージョン、サプライヤ、ライセンス
- 依存と原産地
- 脆弱性とパッチ状況
- 使用期限、使用制限、重要性
- 一意識別子、チェックサム、著者情報
これらの最小限の要素を要求することにより、CERT-In は、SBOM が実行可能で、機械が読み取り可能で、監査に対応可能であることを保証する。
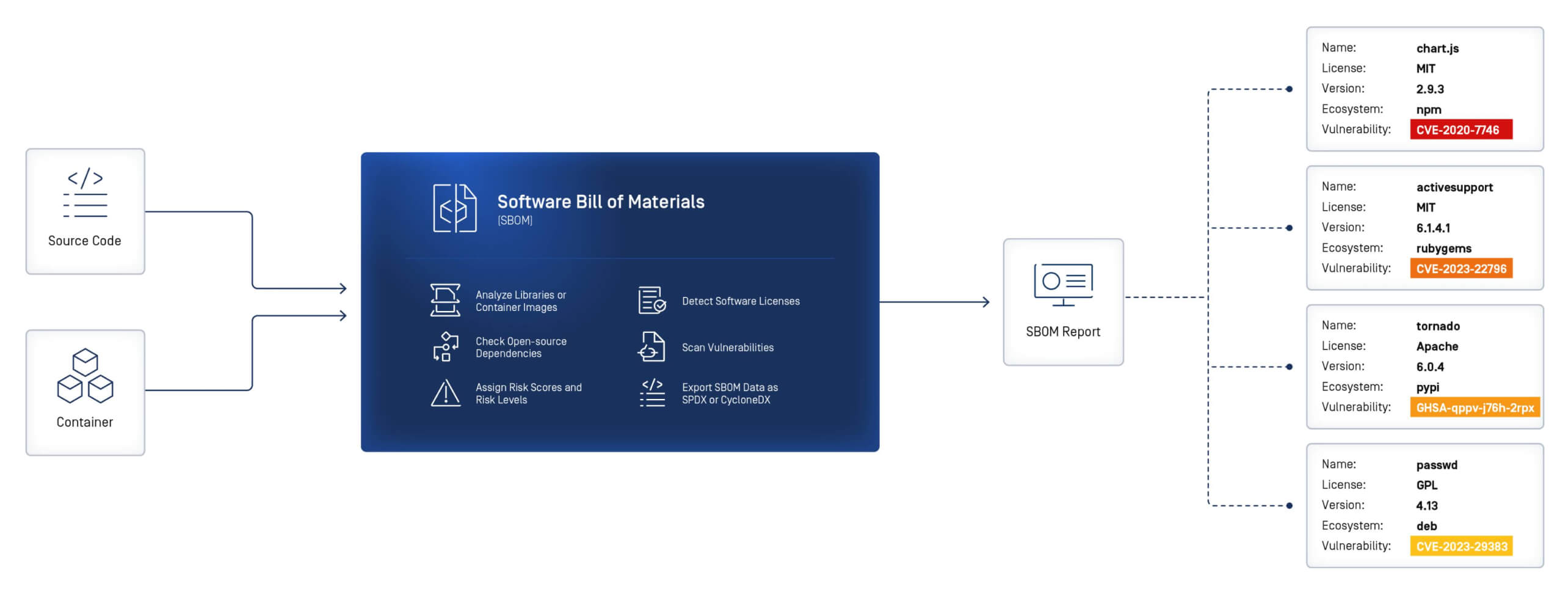
OPSWAT SBOMがCERTイン要件にどのように役立つか
OPSWAT SBOMは、CERT-In SBOMデータ・フィールドの自動化と収集を支援し、ソフトウェア・コンポーネントの詳細、透明性とリスク、およびライセンスと使用法に至るまで、主要な領域にわたって可視性と透明性を提供します。
Software コンポーネントの詳細
- コンポーネント名:ソフトウェア・コンポーネントまたはライブラリの名前。
- コンポーネントのバージョン:コンポーネントのバージョン番号または識別子。
- コンポーネント・サプライヤー:コンポーネントを提供する事業者(ベンダー、サードパーティ、オープンソース)。
- コンポーネントの起源:コンポーネントの出所(プロプライエタリ、オープンソース、サードパーティ)。
- 一意の識別子:バージョンや所有者を超えてコンポーネントを追跡するための識別コード。
- SBOM データの作成者:SBOM エントリの作成に責任を持つエンティティ。
- タイムスタンプ:SBOM エントリが記録された日時。
Software 透明性とリスク
- コンポーネントの依存関係:このコンポーネントが依存している他のコンポーネントやライブラリ。
- 脆弱性:そのコンポーネントに関連する既知のセキュリティ問題(深刻度と CVE 参照)。
- パッチのステータス脆弱性に対する現在のアップデートまたはパッチの提供状況。
- チェックサムまたはハッシュ:ファイルの完全性を検証するための暗号値。
- 実行可能プロパティ:コンポーネントが実行可能かどうか。
- Archive プロパティ:コンポーネントがアーカイブファイルとしてパッケージ化されているかどうか。
- リリース日:コンポーネントが最初にリリースされた日付。
ライセンスと使用
- コンポーネントのライセンス:コンポーネントの使用を規定するライセンスの種類と条件。
- 使用上の制限:コンポーネントの使用に関する法的または規制上の制限。
Software コンポーネントの CERT-In SBOM コンプライアンスへの適合
CERT-In コンプライアンスの達成は、開発、セキュリティ、運用、およびコンプライアンスの各チーム間の調整を必要とする、段階的な道のりである。各関係者は、ソフトウェアライフサイクルのさまざまな時点で SBOM を作成、維持、共有する役割を果たす。
CERT-In 技術ガイドラインの内容と例を含む以下の表は、SBOM 責任が一般的なソフトウェア構成要素とどのように整合するかを示している:
| コンポーネントSoftwareソフトウェア | 例 | SBOMレベル | SBOM著者 | なぜですか? |
|---|---|---|---|---|
| 主な用途 | データ分析アプリケーション | アプリケーションレベルSBOM | 製品開発チームが作成 | 完全なSBOMをアプリケーションと共に顧客または規制当局に提供 |
| 主要Software コンポーネント [データベース、フレームワーク] | PostgreSQL | トップレベルSBOM | ベンダーがSBOMを提供しない場合は、内部で開発する。 | 重要部品のトレーサビリティの確保 |
| プラットフォーム/ミドルウェア [ウェブサーバー、ランタイム環境など] | Apache TomcatServer | デリバリーSBOM | プラットフォーム/ベンダーが提供 | 調達時に共有、ベンダー提供のコンポーネントを統合 |
| サードパーティライブラリ/SDK | Postfix & Twilio SDK | 推移的SBOM | 上流プロバイダーが作成、または利用できない場合は内部で作成 | 間接的な依存関係と外部サービスをカバー |
役割と責任を明確にすることで、組織はコンプライアンスの実践的なステップに移行することができる。段階的なロードマップは、人材、プロセス、およびテクノロジー全体にわたって成熟度を高めるのに役立つ。
1.準備アセスメントとギャップ分析の実施
ソフトウェアインベントリ、脆弱性追跡、およびベンダーが提供する SBOM に関する現在の慣行を特定する。これらを、CERT-In の必須データフィールドおよび形式と照合する。
2.社内のSBOM方針とガバナンス体制の構築
開発者、IT オペレーション、調達、セキュリティ、およびコンプライアンスチームの役割を明確に定義する。ガバナンスにより、SBOM が一貫して作成、維持され、企業全体で共有されるようにする。
3.SBOM生成ツールの選択と実装
自動化は極めて重要である。ツールは必要だ:
- 新しいリリース、パッチ、アップデートのたびにSBOMを生成する。
- DevOpsパイプライン、ソースリポジトリ、コンテナレジストリと統合する。
- CycloneDXおよびSPDX形式で出力し、規制当局のアライメントに対応
4.SBOM ワークフローを SDLC と調達に統合する。
SBOM 生成を SDLC の各段階に組み込む:
- 設計SBOM:計画されたコンポーネント
- ソースSBOM:開発依存関係
- SBOMのビルド:コンパイル中
- 分析対象SBOM:建設後の検査
- デプロイされたSBOM:インストールされた環境
- ランタイムSBOM:アクティブ・コンポーネントの監視
調達契約は、すべてのサプライヤーからのSBOM納入を義務付けるべきである。
5.継続的なコンプライアンスと監査態勢の維持
SBOMの継続的な更新を確立し、VEX(Vulnerability Exploitability eXchange)やCSAFのような脆弱性アドバイザリーと統合し、暗号化、HTTPS、デジタル署名によって安全な保管と共有を確保する。
セキュリティ戦略にSBOMを活用する方法を知りたいですか?
CERT-Inの下で受け入れられたSBOMフォーマットと技術標準
CycloneDXとSPDX:認められたスタンダード
CERT-In は、CycloneDX と SPDX を、SBOM 自動化のための主要な機械可読形式として認識している。
- CycloneDX:軽量、セキュリティ中心、脆弱性管理に最適化
- SPDX:ライセンスを重視し、コンプライアンス文書に広く採用されている
CERT-In SBOM コンプライアンス・ベンダーまたはソリューションの評価と選択方法
適切なベンダーやソリューションを選択することは、コンプライアンスと業務効率の両面で極めて重要である。
CERT-In SBOM コンプライアンス・ベンダーの主な評価基準
- SPDXとCycloneDXのサポート
- DevOpsパイプラインおよびCI/CDワークフローとの統合
- 複数のSBOMレベル(設計、ビルド、デプロイ、ランタイム)を生成する能力
- 監査対応レポートと安全な共有メカニズム
CERT-Inアライメントについてベンダー候補に尋ねるべき質問
適切なパートナーを選択することは、社内の SBOM プロセスを構築することと同様に重要である。CIOと調達リーダーは、RFPとデューデリジェンスのチェックリストの一部として、CERT-Inの整合性を含めるべきである。主な質問は以下の通りである:
- CERT-Inが承認した形式(SPDX、CycloneDX)でSBOMを提供しているか。
- SBOMの更新頻度は、リリース時のみか、継続的か。
- SBOMの生成、検証、安全な共有のために、どのような自動化を提供していますか?
- 安全なSBOM配布(暗号化、RBAC、デジタル署名など)をどのように実施するか。
- 貴社のソリューションは、DevOpsパイプライン、脆弱性データベース、CERT-In勧告と統合されていますか?
- コンプライアンス監査と継続的な規制当局への報告をどのようにサポートしていますか?
このような質問を前もってすることは、ベンダーが書類上のコンプライアンスだけでなく、CERT-Inの進化するガイドラインに沿ったSBOMの実践を持続できることを保証するのに役立ちます。
ベンダーの選定とオンボーディングのためのチェックリスト
- CERT-Inの必須データフィールドとフォーマットに対応
- 生成、追跡、更新の自動化
- 役割ベースのアクセス制御と安全な共有を提供
- 規制産業での採用実績
シームレスなSBOM実装のベストプラクティス
大企業のための実証済みの戦略
- 基礎的なワークフローから始め、時間をかけて成熟度を高める
- すべての調達契約においてSBOMの提供を義務付ける
- SBOM 生成を SDLC の早い段階で統合することにより、シフトレフトアプローチを採用する。
- SBOMの認識と規制要件についてスタッフを教育する
よくある間違いとそれを避ける方法
組織が表面的に取り組めば、善意の SBOM イニシアチブでさえ失敗する可能性がある。CERT-In は、SBOM は正確で、包括的で、継続的に更新されなければならないと強調している。ここでは、最も一般的な落とし穴のいくつかと、それを回避する方法を紹介する:
| よくある間違い | 説明 | それを避けるには |
|---|---|---|
| SBOMを静的レポートとして扱う | 多くの組織は、リリース時にSBOMを作成し、それを更新することはない。これでは、パッチ、更新、または新しい依存関係によってもたらされる脆弱性が見えないままである。 | SBOMを生きたインベントリとして扱う。CI/CDパイプラインを通じて更新を自動化し、新しいビルドまたはリリースごとにSBOMデータが更新されるようにする。 |
| 推移的依存関係を含めない | 他の依存関係によって引き込まれたオープンソースライブラリのような間接的なコンポーネントを見落とすことは、攻撃者が悪用する危険な盲点を生み出す。 | すべての直接依存関係と推移的依存関係を再帰的にマッピングする自動SBOM生成ツールを使用して、ソフトウェア・サプライ・チェーン全体の完全なカバレッジを確保します。 |
| 自動化せずに手作業に頼る | 手作業によるSBOMのコンパイルは、時間がかかり、エラーが発生しやすく、企業規模では持続不可能である。また、一貫性のないフォーマットのリスクも増大する。 | 自動化と標準化の統合。SPDXやCycloneDXのようなCERT-Inが承認したフォーマットでSBOMを生成するツールを採用し、リリース前に検証を実施する。 |
このような間違いを回避し、SBOMの実践を日々の開発ワークフローに組み込むことで、組織はコンプライアンスを戦略的優位性に変えることができ、CERT-In要件を満たしながらリスクを低減することができる。
監査の準備
完全な SBOM リポジトリを維持し、ガバナンス慣行を文書化し、CERT-In 監査テンプレートと整合させる。
規制の変化に対する将来の備え
CERT-Inのロードマップはすでに、より広範なBOM要件(ハードウェア、AI、クラウド)を示唆している。スケーラブルで柔軟なツールを採用する企業が、最も適応しやすい立場にあるだろう。
自動化、遵守、保護:SBOM管理へのOPSWAT アプローチ
OPSWAT SBOM
OPSWAT SBOMは、ソースコードやコンテナ内のソフトウェアコンポーネントの正確なインベントリを提供することで、開発者を支援します。開発速度に影響を与えることなく、攻撃者の先を行き、脅威を発見し、脆弱性を検出します。
Software パッケージと成果物のSBOM
ソフトウェア開発チームが、オープンソースの依存関係のセキュリティ脆弱性とライセンスに関する懸念を特定し、優先順位を付け、対処できるようにする。
Software パッケージと成果物のSBOM
ソフトウェア開発チームが、オープンソースの依存関係のセキュリティ脆弱性とライセンスに関する懸念を特定し、優先順位を付け、対処できるようにする。
Container イメージ用SBOM
コンテナイメージを分析し、パッケージ名、バージョン情報、潜在的な脆弱性の SBOM を生成します。
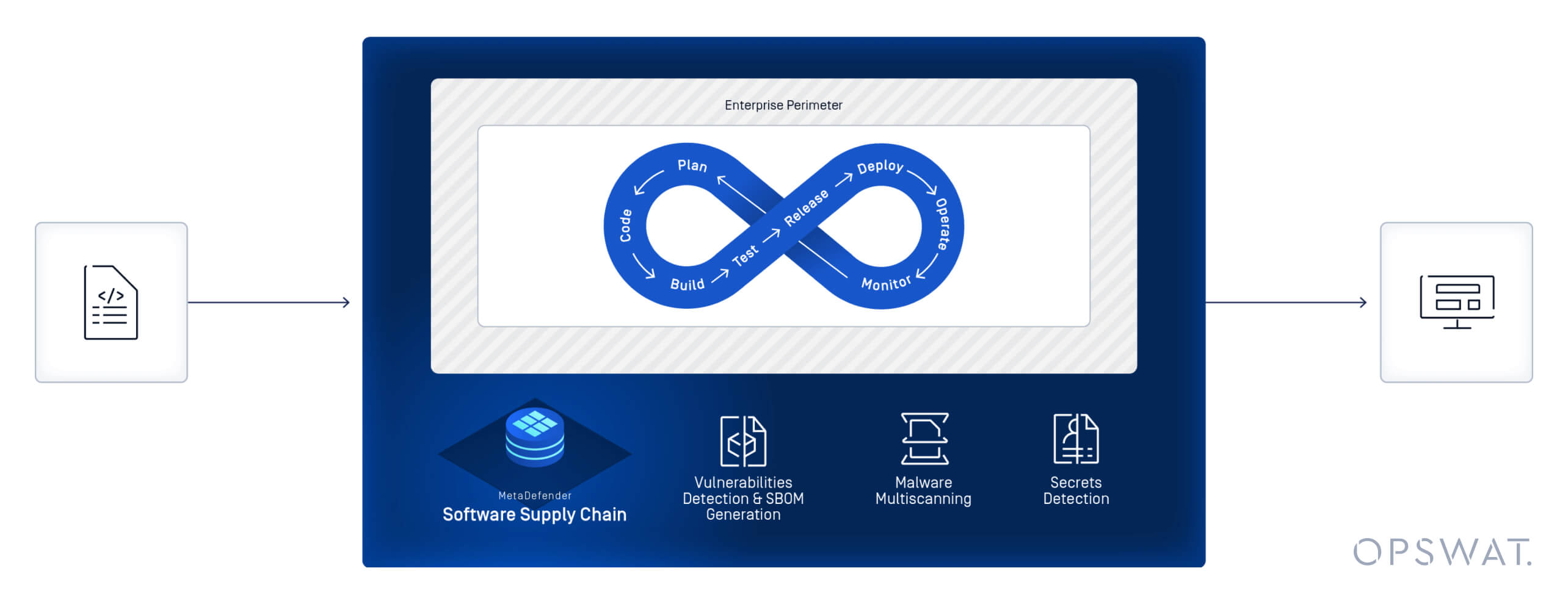
MetaDefender Software Supply Chain™
SBOMコンプライアンスを超えて、高度に進化するソフトウェアサプライチェーン攻撃に対処する。
OPSWAT MetaDefender Software Supply Chainは、サプライチェーンリスクに対する拡張された可視性と強固な防御を提供します。MetaDefenderのゼロトラスト脅威検出・防止技術により、ソフトウェア開発ライフサイクル(SDLC)はマルウェアや脆弱性から保護され、アプリケーションセキュリティとコンプライアンス遵守が強化されます。
コードからマルウェアを検出する
30以上のアンチウイルスエンジンを組み合わせることで、検出率を高め、マルウェアがワークステーション、コンテナ、ソースコードに感染するのを効果的に防ぎます。
ハードコードされた秘密を特定する
Proactive DLPTM は、ソースコードに残されたパスワード、シークレット、トークン、API キーなどの機密情報を識別します。
Supply Chain 攻撃からコンテナをSecure
コンテナ・イメージの各レイヤーの下に存在するマルウェア、脆弱性、その他の潜在的リスクを評価し、評価する。
シンプルな統合
チームがソースコードリポジトリ、コンテナレジストリ、バイナリサービス、またはそれらのツールの組み合わせを使用しているかどうかに関わらず、MetaDefender Software Supply Chain SDLC全体を通して安全性を確保するために、一般的なプラットフォームとのネイティブな統合を提供します。
よくある質問
CERT-In SBOM ガイドラインに違反した場合、どのような罰則が適用されるのか。
規制当局による監査や、政府や重要なサービスとの契約が制限される可能性。CERT-In SBOM のガイドラインに準拠していない場合、組織はデータ漏洩の危険にさらされ、多額の罰金を科される可能性がある。
SBOMの更新頻度は?
新しいリリース、アップデート、パッチ、ベンダーの変更のたびに。
オープンソースやサードパーティのコンポーネントを含めることは可能か?
そうだ。すべての依存関係(直接的および推移的)を完全に可視化することは必須である。
中小企業は免除されるのか?
規制対象外の新興企業は救済措置が限定的かもしれないが、採用は強く推奨される。
CERT-Inはどのようにグローバルスタンダードと整合しているのか?
インドのアプローチは、NISTや EUサイバーレジリエンス法のような国際的なフレームワークを反映し、国境を越えた互換性を確保している。
脆弱性の開示はどのように扱われるべきか?
VEXおよびCSAF勧告を通じ、CERT-Inアラートおよび内部SBOMシステムと統合。
オートメーションが果たす役割とは?
自動化により、継続的なコンプライアンスが可能になり、人的ミスが減り、ハイブリッドIT環境でのスケーラビリティが確保される。
セクター別の考察:金融機関、Supply Chain、重要インフラストラクチャー
金融
銀行やNBFCは、SBOMの慣行をRBIのサイバーセキュリティ指令と整合させ、機密データの取り扱いに関する監査要件を厳格化する必要がある。
Supply Chain
サプライヤーは、契約の一部として SBOM を提供しなければならない。組織は、透明性とリスク管理のために、内部および外部の SBOM インベントリを維持しなければならない。
重要インフラ
電気通信、防衛、エネルギーなどのセクターは、規制の重複に直面している。SBOM の実践は、システムの強靭性と国家安全保障に関するより広範な枠組みと統合されなければならない。
次なる課題は?サートインSBOMガイドラインへの備えが不可欠
CERT-In SBOM ガイドラインは、インド企業にとって転機となるものである。当初はSBOMに焦点を絞ったものであったが、現在ではソフトウェア・サプライチェーンの可視化とリスク管理のための包括的な枠組みへと拡大している。
OPSWAT SBOMテクノロジーは、コンプライアンスを超えて、SDLC全体にサプライチェーンの可視性を組み込み、コードリポジトリ、コンテナレジストリ、DevOpsパイプラインと多層セキュリティを統合します。
OPSWAT CERT-In SBOMへの準拠を簡素化し、ソフトウェア・サプライチェーンの安全性を確保するためにどのような支援を提供できるかをご覧ください。



