CVE-2025-66516は、2025年12月4日に初めて発見されたApache Tikaの重大な脆弱性(NVDによる深刻度スコア9.8)であり、広く利用されるバックエンドコンポーネントの単一欠陥が現代のアプリケーション全体に及ぼす甚大な影響を浮き彫りにしています。 Apache Tikaは、インデックス作成、検索、コンプライアンス、コンテンツ分析のための文書処理ワークフロー(PDF、PPT、XLS)に深く組み込まれており、システムやデータへの広範なアクセス権を持ちながら、しばしばバックグラウンドで動作します。このレイヤーで脆弱性が発生すると、影響を受けるライブラリがエンドユーザーに直接公開されていなくても、環境全体が危険にさらされる可能性があります。
パッチ適用のみに依存するだけでは、この種の重大な脆弱性に対する防御策として不十分です。組織は脆弱性が発生することを前提とし、各段階でのリスク露出の低減に焦点を当てた多層的なセキュリティアプローチを必要としています。
このブログでは、3つの補完的な層を検証します:
- Sanitizing untrusted PDF files before they are processed with Deep CDR™ Technology
- ゼロデイ検出による高度な分析を通じた悪意のある文書動作の検知
- ソフトウェアサプライチェーンの保護:SBOM(ソフトウェア部品表)とSCA(ソフトウェア構成分析)によるApache Tika依存関係における重大なXXE脆弱性の検出
これらの層が一体となって、既知の脆弱性と将来のファイルベースの脅威の両方を軽減するための実用的な多重防御戦略を提供します。
1. File Sanitization with Deep CDR™ Technology
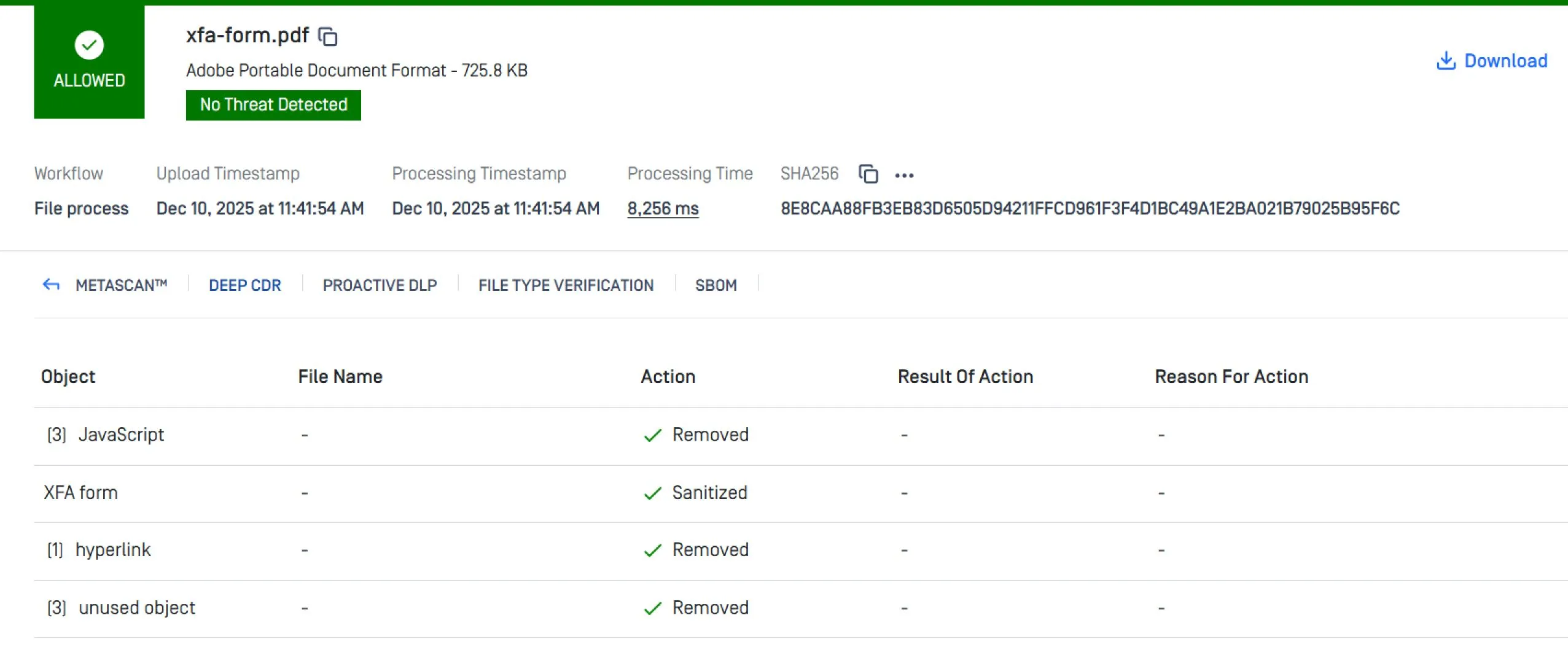
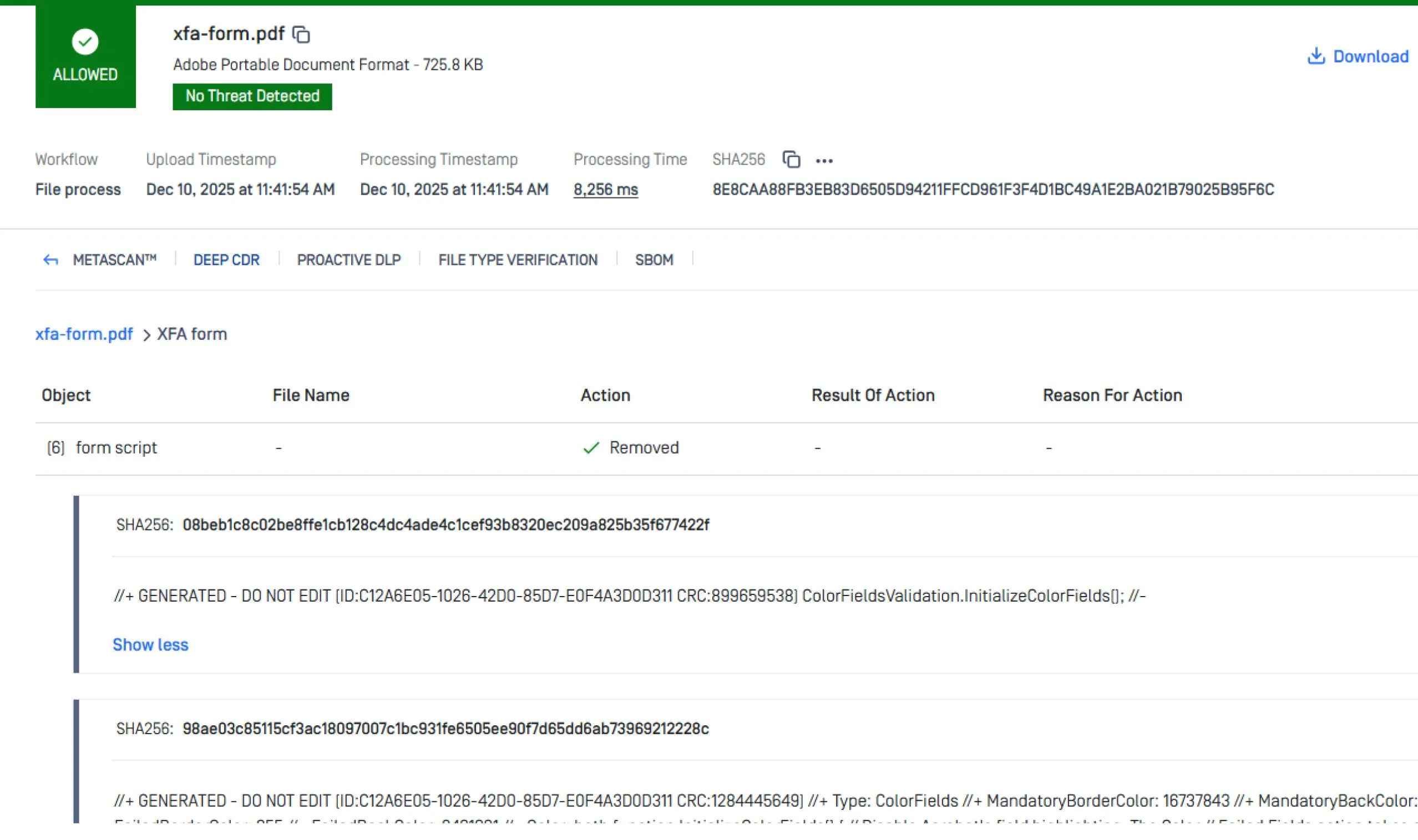
A tactical solution to mitigate CVE-2025-66516 is to sanitize all incoming PDF files before they reach Apache Tika. Deep CDR™ Technology (OPSWAT’s content disarm and reconstruction technology) removes embedded XFA forms, external entity references, and any other active content that could trigger XXE attacks.
The sanitized output is a safe, regenerated PDF containing only the approved, non-executable elements. This pre-processing layer ensures that even maliciously crafted PDFs are neutralized before Tika performs parsing or metadata extraction. Learn more about OPSWAT Deep CDR™ Technology
2. ゼロデイ検知を伴う行動分析
高度な検出ルールと実行時エミュレーションを組み合わせることで、OPSWAT独自のエミュレーションベースのサンドボックス技術OPSWAT、エクスプロイトが難読化されていたり複雑なファイル構造に埋め込まれていたりする場合でも、静的解析では見逃される可能性のある悪意のある動作を観察できます。Filescan.IO - 次世代マルウェア分析プラットフォームでご確認ください。
脆弱性の開示やベンダーのパッチは、ゼロデイ攻撃のペースに追いつけないことが多々あります。OPSWAT 、組み込みの脅威インテリジェンスOPSWAT 動的解析OPSWAT 、それらを検知・防止します。ソフトウェアによる緩和策に依存する代わりに、当社の技術はPDFファイルの深いファイルレベル解析を行い、その動作や悪用しようとするシステム機能(危険なXML外部エンティティを参照する埋め込みXFAフォームなど)を理解します。
これにより、実際の攻撃の影響によって評価された構造的異常、既知の悪用手法、さらには文書化されていない、または新たなセキュリティ上の欠陥に依存するゼロデイ攻撃の検出が可能になります。 OPSWAT 検出の詳細をご覧ください。
3.Software Supply Chain Secure
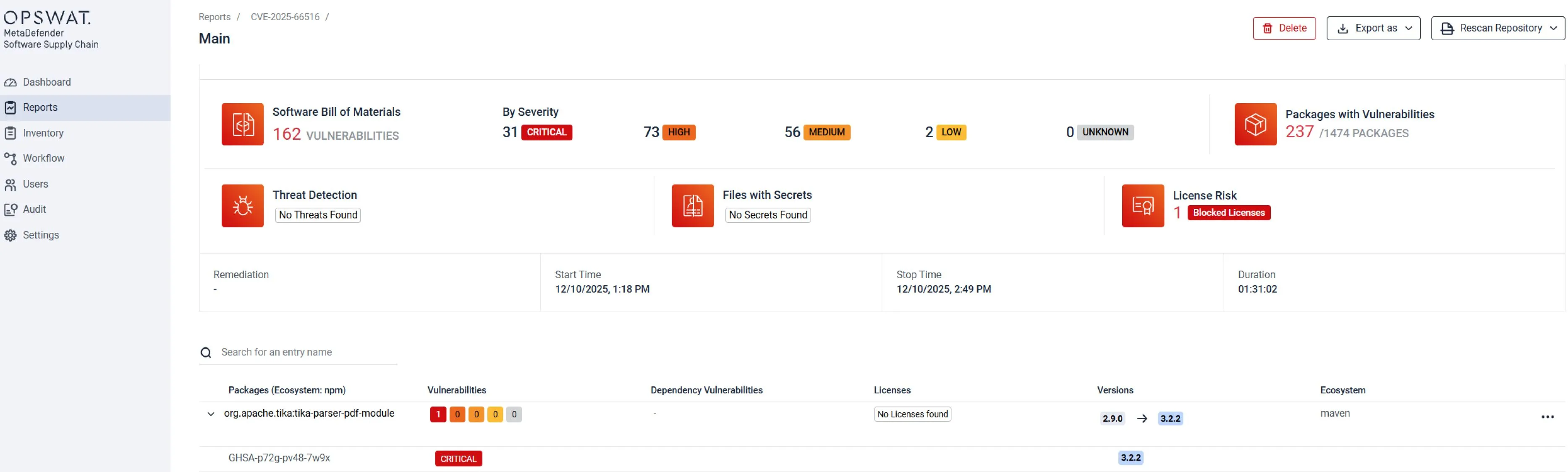
セキュアなソフトウェア供給チェーンプロセスは、サービスやコンポーネントがCVE-2025-66516の影響を受ける脆弱なApache Tikaバージョンに依存しているかどうかを特定するのに役立ちます。
SCA(ソフトウェア構成分析)などの自動依存関係スキャンツールをCI/CDパイプラインに統合することで、組織はTika ≤ 3.2.1を参照している古いライブラリ、推移的依存関係、または隠れたモジュールを継続的に検出できます。 OPSWAT MetaDefender Software Supply Chain詳細についてはこちらをご覧ください。
これらのスキャナーは脆弱なバージョンを早期に検知し、チームがデプロイをブロックしたり、Tika 3.2.2のようなパッチ適用済みリリースへの強制アップグレードを実行できるようにします。
SBOM(ソフトウェア部品表)の生成と定期的な在庫監査と組み合わせることで、このアプローチはサードパーティ製ライブラリへの完全な可視性を確保し、脆弱なコードが本番環境に流入するリスクを低減します。
多層セキュリティが重要な理由
CVE-2025-66516は、現代の攻撃が単一の脆弱性に依存することは稀であることを示している。代わりに、信頼されたファイル形式、信頼された解析ライブラリ、信頼された自動化ワークフローを悪用する。これらの前提条件のいずれかが崩れると、下流システムがリスクを継承する。これが、パッチ適用や境界防御のみに依存することがもはや不十分である理由である。
多層的なセキュリティモデル(しばしば深度防御と呼ばれる)は、制御が最終的には失敗すると想定し、それに応じて保護策を設計する:
- パッチ適用が遅延または不完全な場合、入力ファイルのサニタイズ処理により、XFAフォームや外部エンティティ参照などの危険なコンテンツが脆弱なコードに到達する前に除去されます。
- 悪意のあるファイルが静的チェックを回避した場合でも、行動分析とエミュレーションは既知のシグネチャではなく実際の実行動作に基づいてエクスプロイトの試みを検出できる。
- 依存関係を通じて安全でないコードが環境に流入した場合、セキュアなソフトウェア供給チェーンの実践により可視性と強制力が提供され、脆弱なコンポーネントが最初からデプロイされるのを防止します。
これらの各層は、攻撃ライフサイクルの異なる段階に対応しています:解析前、実行中、そして開発およびデプロイプロセス全体を通じてです。これらが連携することで、悪用される可能性と、システムが既に本番環境にある後に脆弱性が発見された場合の被害範囲の両方を低減します。
信頼できないファイルを大規模に処理する組織、特に自動化されたバックエンドサービスにおいては、この多層的なアプローチが不可欠です。CVE-2025-66516のような脆弱性は今後も出現し続けるでしょうが、多層的なセキュリティ対策が整っていれば、それらは致命的な障害ではなく管理可能なリスクとなります。
Apache Tikaについて
Apache Tikaは、PDF、Word、PowerPointなど様々な種類のファイルを取り込み、テキストやメタデータを抽出するJavaライブラリです。これにより、アプリケーションが文書をインデックス化、検索、分析できるようになります。検索エンジン、eディスカバリーツール、ユーザーが文書をアップロードして自動処理できるあらゆるWebアプリケーションなど、幅広いシステムで利用されています。
CVE-2025-66516 について
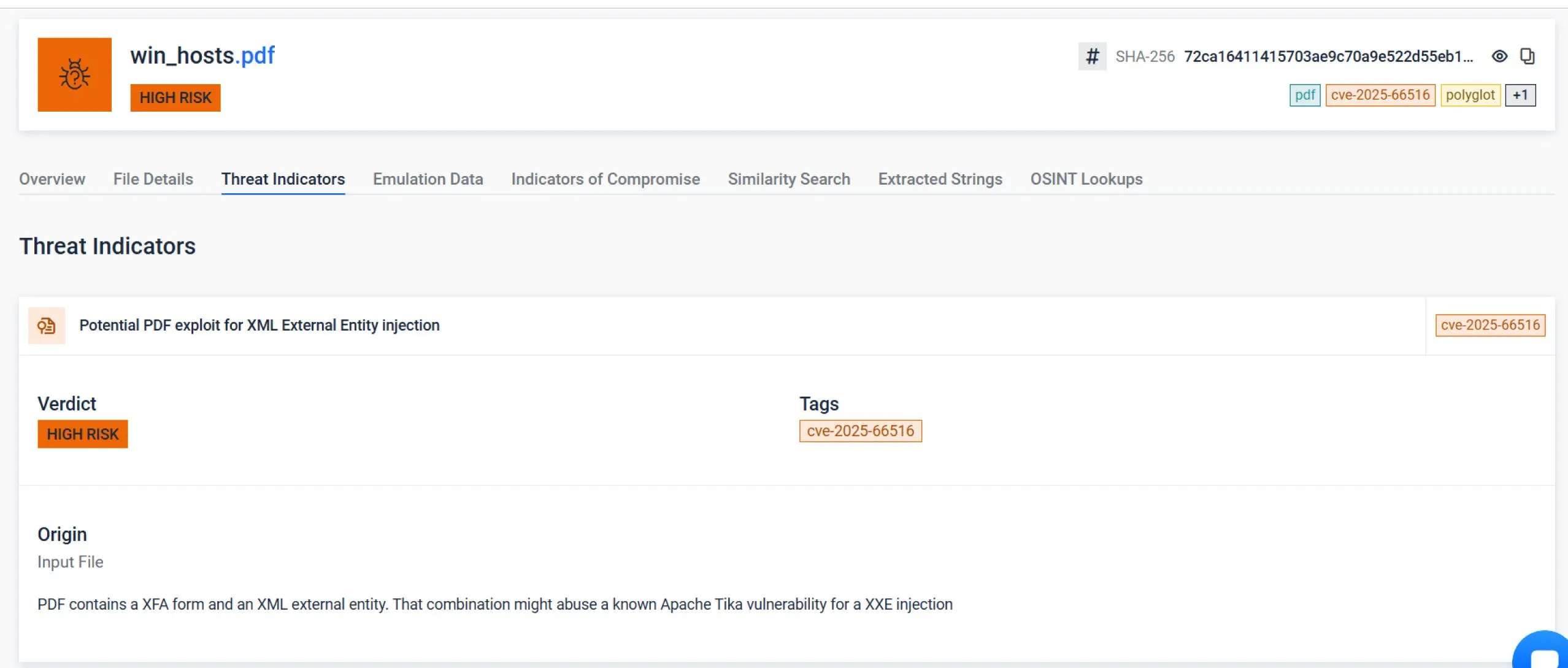
攻撃対象領域は、Tikaが悪意のあるXFA(XML Forms Architecture)フォームを含むPDFを解析する際に発動するXXE(XML外部エンティティ)脆弱性である。XXEとは、TikaがPDF内のXMLを処理する際に、ローカルファイルやリモートURLを指す「外部エンティティ」を意図せず読み込むように仕向けられることを意味する。これは本来発生すべきではない動作である。
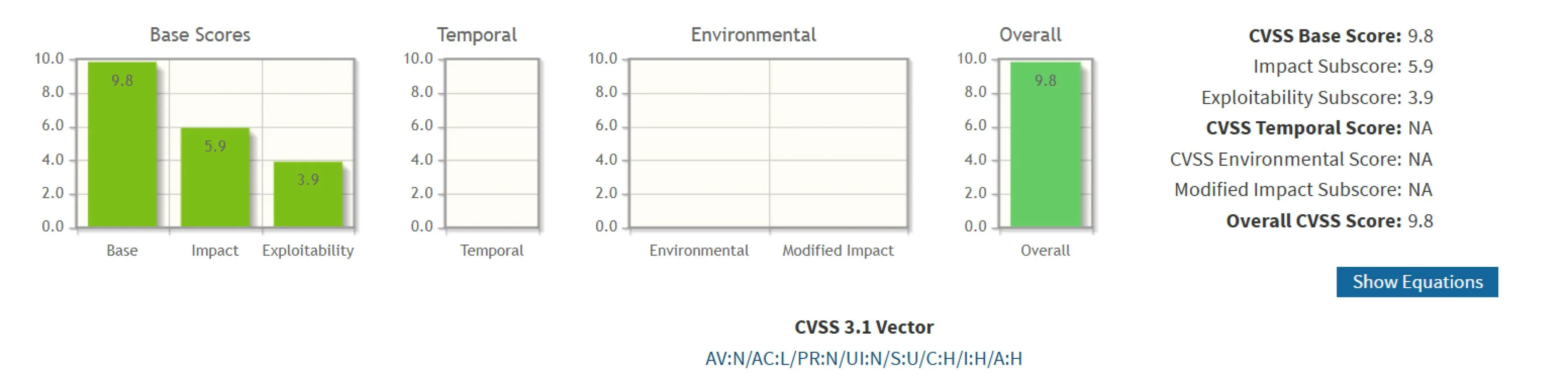
CVE-2025-66516は、Apache Tikaにおける重大なセキュリティ脆弱性であり、攻撃者が悪意のあるXFAフォームを含む細工されたPDFを送信することでXXEインジェクションを引き起こすことが可能です。この脆弱性は複数のモジュール(tika-core バージョン 3.2.1 以下、tika-pdf-module、tika-parsers)に影響し、CVSS 9.8 の深刻度評価を受けています。悪用された場合、攻撃者は機密性の高いサーバーファイルの読み取り、サーバーサイドリクエストフォージェリ(SSRF)の実行、さらにはリモートコード実行を達成する可能性があります。
この場合、脆弱性はPDFパーサーモジュールだけでなく、コアとなるTikaライブラリ(tika-core)に存在するため、PDFモジュールのみを更新しても不十分です。
リスクのある典型的な使用事例
ユーザーがPDFをアップロードしてプレビュー、インデックス作成、テキスト抽出を行えるアプリケーション、またはバックグラウンドでTikaを使用してそれらのアップロードを自動的に処理するアプリケーションは、特に内部ネットワークや機密ファイルへのアクセス権を持つバックエンドサービスで実行されている場合、リスクにさらされています。

