ファイルベースの攻撃やゼロデイ脅威が増加し、アンチウイルスやサンドボックスのような従来のセキュリティ・ソリューションの有効性が損なわれつつあります。CISOは今日、特に文書、添付ファイル、ファイル転送が日常業務に不可欠な環境において、高度な攻撃者に対するプロアクティブな防御を証明する必要に迫られています。
そこで、CDR(Content Disarm and Reconstruction)が登場します。CDRは、既知のマルウェアを検出しようとするのではなく、ユーザビリティを維持しながら、悪意のある可能性のあるコンポーネントを削除することで、ファイルをプロアクティブにサニタイズします。
このブログでは、CDRの技術的特徴とその仕組み、レガシー・ツールとの比較、そして企業が多層防御戦略の一環としてCDRを急速に採用している理由について解説します。
CDRとは何か?
CDRは、ファイルから悪意のあるアーティファクトを除去することで、潜在的な脅威を無効化するプロアクティブなファイルサニタイズ技術です。CDRは、マルウェアを特定するのではなく、ファイルを逆アセンブルし、マクロや埋め込みコードのような安全でない要素を取り除き、エンドユーザー向けに安全で使用可能なバージョンを再構築します。
このアプローチにより、電子メール、ダウンロード、ファイル転送、コラボレーションツールを介して企業に入るファイルに悪意のあるペイロードが隠されていないことを保証し、生産性を妨げることなく組織を保護します。
CDRと従来のマルウェア検出の違い
- CDR:シグネチャや行動分析に頼らずに、承認されていない要素を削除する。
- アンチウイルス:シグネチャまたはヒューリスティックに基づいて既知の脅威を検出する。
- サンドボックス:挙動を観察するため、隔離された環境で不審なファイルを爆発させる。
ほとんどの検出ベースのツールとは異なり、CDRはシグネチャを使用しない保護を提供するため、ゼロデイ脅威やポリモーフィック型マルウェアに対して非常に効果的です。
武装解除と復興のコア原則
- すべてのファイルが信頼できないと仮定します。
- 解除する: アクティブまたは実行可能なコンテンツ(マクロ、スクリプト、埋め込みコード)を削除します。
- 再構築:安全で標準化されたフォーマットでファイルを再生成する。
- 提供する:完全性、機能性、事業継続性を維持した、クリーンで使用可能なファイルを提供する。
現代のサイバーセキュリティにおいてCDRが重要な理由
マルウェアの90%以上は、電子メールの添付ファイル、アップロード・ポータル、ダウンロード、リムーバブル・メディアなど、ファイルベースの脅威を通じて組織に侵入します。攻撃者は、PDF、Office文書、画像などの信頼できるファイルタイプを標的とするようになっているため、検出だけに頼っていると盲点が生じます。CDRは、脅威が実行される前に無力化することで、このギャップを埋めます。
企業がファイル・セキュリティのためにCDRを利用する理由
採用の原動力は以下の通りです。:
- ゼロデイとAPT(高度な持続的脅威)の台頭
- 金融、医療、政府部門におけるコンプライアンスのプレッシャー
- 安全で使いやすいファイルによる事業継続の必要性
- 検出ベースのツールによる偽陽性の低減
- 深層防衛戦略の強化
コンテンツの武装解除と再建はどのように機能するのか?
CDRは、ユーザビリティに影響を与えることなく、リアルタイムでファイルをサニタイズするように設計された、構造化されたワークフローに従っています。
ステップバイステップのCDRワークフロー:ファイルの取り込みから配信まで
- 取り込み:ファイルのアップロード、ダウンロード、転送。
- 解析:ファイルは解析のために構成要素に分解される。
- 解除します:悪意のある、または不要な要素(マクロ、埋め込み実行可能ファイル、スクリプト)は取り除かれます。
- 再構築:ファイルのクリーンで機能的なコピーが再構築される。
- 配送:安全なファイルがエンドユーザーまたはワークフローに渡される。

CDR技術に求められる主な機能
- 幅広いファイル形式をカバー(Office、PDF、画像、アーカイブなど)
- 大容量環境向けのリアルタイム処理
- ポリシーベースのコントロール(隔離、警告、ブロックまたは許可)
- さまざまなユースケースに対応する柔軟な構成(Eメールゲートウェイ、ウェブアップロード、ファイル共有プラットフォーム)
- ファイルの完全性とユーザビリティの維持
Deep CDR 重要な理由
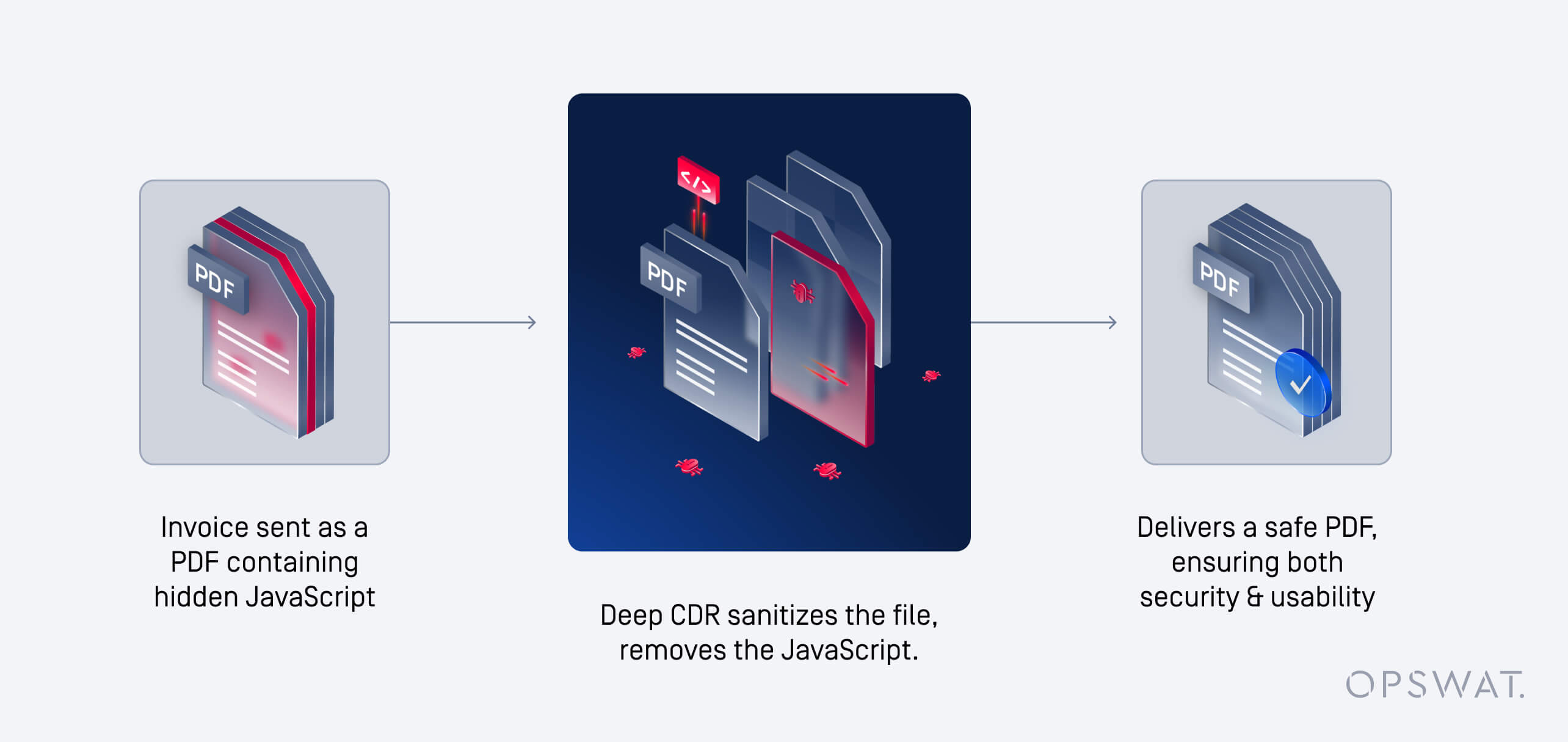
Basic CDRは、表面レベルのアクティブコンテンツを削除します。Deep CDR™はさらに進んで、ネストしたレイヤーに悪意のあるフラグメントが隠れていないことを確認するために、ファイル構造を細かいレベルで解析します。
CDRとアンチウイルスおよびサンドボックスの比較:主な違いと補完的役割
アンチウイルス、サンドボックス、CDRがファイルベースの脅威にどう対処するか
| ユースケース | アンチウイルス | サンドボックス | CDR |
|---|---|---|---|
| 既知の脅威の検出 | 完全サポート | ||
| ゼロデイ・プロテクション | |||
| AIが生成するマルウェア | 一部サポート | ||
| 行動分析学 | |||
| リアルタイム・ファイル・サニタイゼーション | 該当なし | 該当なし | |
| ファイルの使いやすさを維持 | 一部サポート | ||
| コンプライアンスの調整 | 一部サポート | 一部サポート | 一部サポート |
| 大容量のためのスケーラビリティ | 一部サポート | ||
| エンタープライズ・ツールとの統合 |
CDRはサンドボックスとアンチウイルスを置き換えるのか、補完するのか?
CDRはそれ自体で代替するものでも、全体的な解決策でもない。CDRは深層防衛戦略の補完的なレイヤーなのです:
- アンチウイルスは既知の脅威を効率的に処理する。
- サンドボックスは行動インサイトを提供する。
- CDRは、ファイルがユーザーに届く前に未知の脅威からサニタイズされることを保証します。
適切な組み合わせの選択CDR、アンチウイルス、またはその両方を導入するタイミング
- 電子メールの添付ファイルプロアクティブなサニタイズにCDRを使用
- 高度な脅威分析サンドボックスの使用
- Endpoint アンチウイルスの使用
- 企業の回復力:この3つを組み合わせる
CDRはどのようなファイルと脅威に対処するのか?
CDRがサポートする一般的なファイルタイプ
- マイクロソフト・オフィス(ワード、エクセル、パワーポイント)
- 画像 (JPEG, PNG, BMP, ...)
- アーカイブ (ZIP, RAR)
- 実行可能ファイルとインストーラー
- CAD、DICOM、および特殊な業界フォーマット
CDRによって無力化される脅威ベクトル:マクロ、埋め込みオブジェクトなど
- Officeファイルのマクロ
- PDFでのJavaScriptアクション
- ステガノグラフィー
- ファイルリーダーの脆弱性を誘発する悪用可能なオブジェクト
- 難読化またはポリモーフィック化されたペイロード
CDRはどのようにゼロデイ脆弱性(
)と回避的なファイルベースの脅威から保護するのか?
CDRが未知のマルウェアやゼロデイ・マルウェアに有効な理由
- シグネチャや行動パターンに依存しない
- ファイルを直接サニタイズすることで、構造的なリスクを中和します。
- 実行前に攻撃対象領域を減らす
CDRと回避型マルウェアのテクニックの比較
などの回避戦術:
- ポリモーフィック・マルウェア
- 暗号化されたペイロード
- 遅延実行トリガー
CDRは、ファイル・レベルでアクティブなコンテンツを除去し、攻撃者が悪用できるものを何も残さないようにすることで、これらを軽減する。
CDRの評価と実施のためのベストプラクティス
CDR技術ベンダーを選ぶ際の主な評価基準
- 対応ファイルタイプの広さ
- 除菌の深さ(ベーシックとDeep CDR比較)
- 既存のワークフローとの統合機能
- コンプライアンス認証とアライメント
- 規模に応じたパフォーマンス指標
既存のセキュリティ・インフラとCDRの統合
| 落とし穴 | 緩和 |
|---|---|
| 基本的なCDRのみの展開 | 高度な保護のためにDeep CDR 選択する |
| 暗号化ファイルの無視 | ポリシーベースの処理(隔離または手動レビュー)を使用する |
| 貧弱な統合 | 実績のあるエンタープライズ・コネクターを持つベンダーを選ぶ |
OPSWATファイルセキュリティ・ソリューション・スイートと、Deep CDR どのように進化する脅威の一歩先を行く企業を支援できるのか、詳細をご覧ください。
よくある質問
CDRテクノロジーは、文書の使いやすさやフォーマットに影響を与えることがありますか?
OPSWAT Deep CDR 、サニタイズ後のドキュメントの使いやすさと読みやすさを維持するように設計されています。脅威を排除するためにマクロや埋め込みスクリプトなどのアクティブコンテンツは削除されますが、ビジネスの継続性をサポートするために、ファイルのコア構造とフォーマットはそのまま残ります。
CDRは医療や金融のような規制の厳しい業界に適しているか?
はい。OPSWAT Deep CDR 、医療、金融、政府などの業界の厳格なコンプライアンス要件に対応しています。検知に頼ることなくプロアクティブに脅威を除去することで、HIPAA、PCI-DSS、GDPRなどの規制要件をサポートし、企業がデータの完全性と機密性を維持できるよう支援します。
CDRは暗号化されたファイルやパスワードで保護されたファイルをどのように扱うのですか?
暗号化されたファイルやパスワードで保護されたファイルは、復号化しない限りサニタイズできません。OPSWAT Deep CDR 、隔離や手動レビューなどのポリシーベースの処理のためにこれらのファイルにフラグを立て、隠れた脅威がセキュリティ制御をバイパスしないようにします。
CDRの典型的な導入モデル(クラウド、オンプレミス、ハイブリッド)は?
Deep CDR 、多様な企業ニーズに対応するため、複数の導入オプションをサポートしています。厳密なデータレジデンシーや規制要件があるオンプレミス環境では、以下の方法で提供されます。 MetaDefender Core.スケーラブルでインフラストラクチャを必要としないソリューションをお探しの企業には、MetaDefender Coreがお勧めです、 MetaDefender CloudはSaaSサービスとしてCDRを提供します。オンプレミスとクラウドを組み合わせたハイブリッドアプローチも可能で、分散インフラをサポートしたり、ピーク時の処理要求を処理したりすることができます。この柔軟性により、パフォーマンス、コンプライアンス、スケーラビリティを損なうことなく、既存のセキュリティアーキテクチャにシームレスに統合することができます。
CDRはウイルス対策ソフトのように頻繁なアップデートが必要ですか?
シグネチャの更新に依存するウイルス対策ツールとは異なり、OPSWAT Deep CDR 、シグネチャを使用しないプロアクティブなアプローチを採用しています。ファイル構造と挙動に基づいて悪意のあるコンテンツを削除するため、継続的な更新の必要性が減り、運用のオーバーヘッドが最小限に抑えられます。
CDRは大容量のファイルをどのくらい速く処理できますか?
OPSWAT Deep CDR 、ハイパフォーマンス環境向けに設計されています。大量のファイルをリアルタイムで処理できるため、待ち時間を発生させることなく、電子メールのフィルタリング、ファイルのアップロード、クロスドメイン転送などのユースケースに適しています。 Deep CDR パフォーマンスメトリクスを見る。
CDRはEメールゲートウェイやファイル共有プラットフォームと統合できるか?
はい。OPSWAT Deep CDR 、セキュアな電子メールゲートウェイ、ファイル共有プラットフォーム、およびコンテンツコラボレーションツールとシームレスに統合します。これにより、企業は重要な出入口でファイルをサニタイズすることができ、コミュニケーション・チャネル全体でファイルベースの脅威のリスクを低減することができます。
機密文書にCDRを使用することのプライバシーへの影響は?
OPSWAT Deep CDR 、プライバシーを考慮して構築されています。ファイルをインメモリで処理し、サニタイズされたコンテンツを保持しないため、機密データを安全に取り扱うことができます。組織は、プライバシー要件を満たすために、特定のメタデータやフィールドを処理から除外するポリシーを設定できます。
新しいファイル形式や脅威に対応するために、CDRテクノロジーはどのように進化するのか?
OPSWAT Deep CDR 継続的に更新し、新しいファイル形式や進化する脅威ベクトルをサポートしています。その形式にとらわれないアーキテクチャにより、見慣れないファイル構造や変更されたファイル構造であっても脅威を無効化することができ、将来の攻撃手法に対しても強靭です。
CDRテクノロジーはAIが生成した、あるいはAIを搭載したマルウェアを防御できるのか?
そうです。OPSWAT Deep CDR 、AIによって生成または強化されたものを含め、脅威の生成方法に関係なく脅威を無力化します。既知のシグネチャや行動パターンに依存する検出ベースのツールとは異なり、Deep CDR 構造解析に基づいてファイルから悪意のある可能性のある要素を削除します。このため、従来のセキュリティソリューションを回避する可能性のある、新規の、ポリモーフィックな、またはAIによって作成されたマルウェアに対して非常に効果的です。

